Is the upper diagram close to what you have today? consider a change.
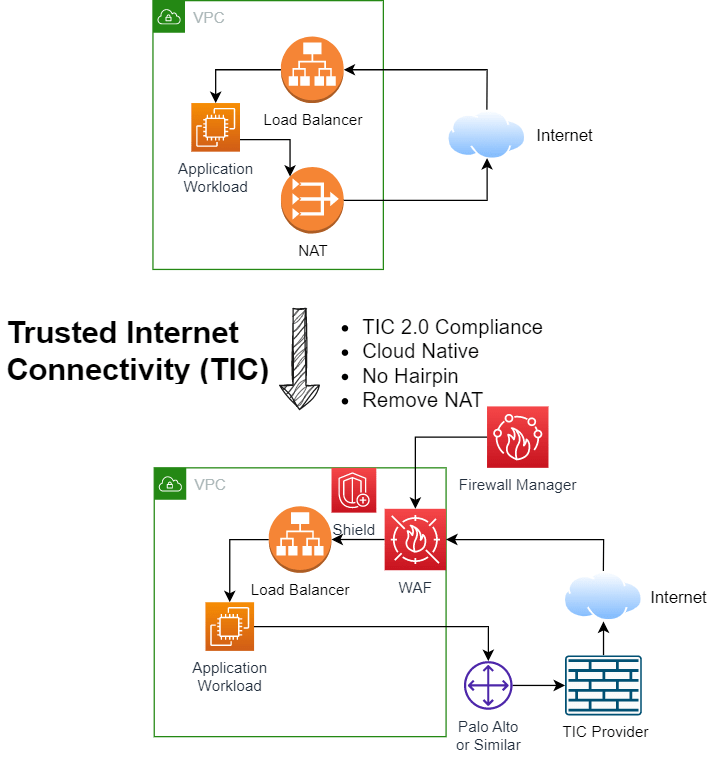
This design illustrates how to secure cloud workload, achieve compliance, without sacrificing performance and cost. Many industries are mandated by specific trusted internet connectivity (TIC) requirement. Some overhauls the network traffic to on premise (Hairpin), which loses the benefit of using cloud.
The top picture is what one’s recreational cloud use look like, and some early stage adopters might have similar implementation. The bottom picture is what you supposed to be, in a secured and compliance way.
This work is crucial for cloud security. It is:
- From non-compliance to compliance
- From “open to be attacked” to “open to business in a secured way”
- From NO TIC to TIC 2.0, heading to TIC 3.0.
- From an early establishment of cloud to enterprise cloud
- From “I don’t know” to “you can’t hide”
- Improvement in all paradigms: cloud native (operation), no hairpin (performance), remove NAT (cost reduction), compliance (cyber)
Viva craftsmanship!