This is the last episode of the infrastructure series, after a theme on the data format, the technologies, and cloud native options, I use the same U shaped transaction flow and mark related cyber security practices on the map.
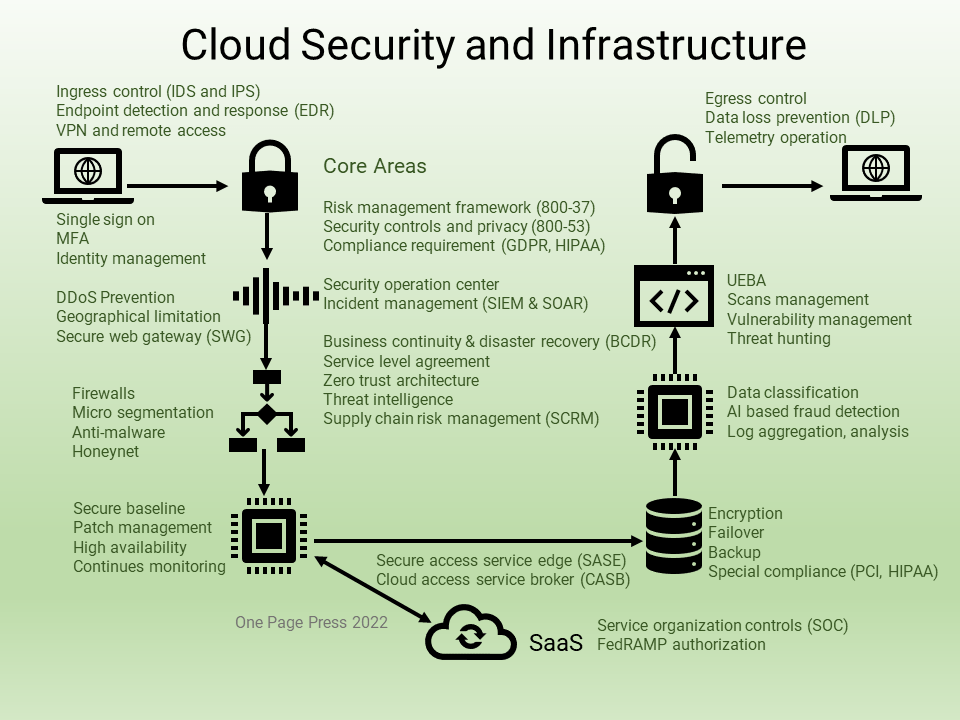
The cybersecurity industry uses a model referred to as the security triad, also known as CIA: Confidentiality, Integrity, and Availability.
Cybersecurity practices include organization compliance. policies, and operations to protect information from being stolen, compromised or attacked.
As a concept, this picture is self-explanatory. It concentrates core cyber practices in the middle as the strategic group, and places other tactical and operational items along with individual areas according to the technology stack.