The OWASP® Foundation released Software Assurance Maturity Model (SAMM) 2.0 last week. This framework targets to build better security posture for all organizations that conduct software development activities, which is a use case of baking security deep into SDLC, regardless of your chosen flavor.
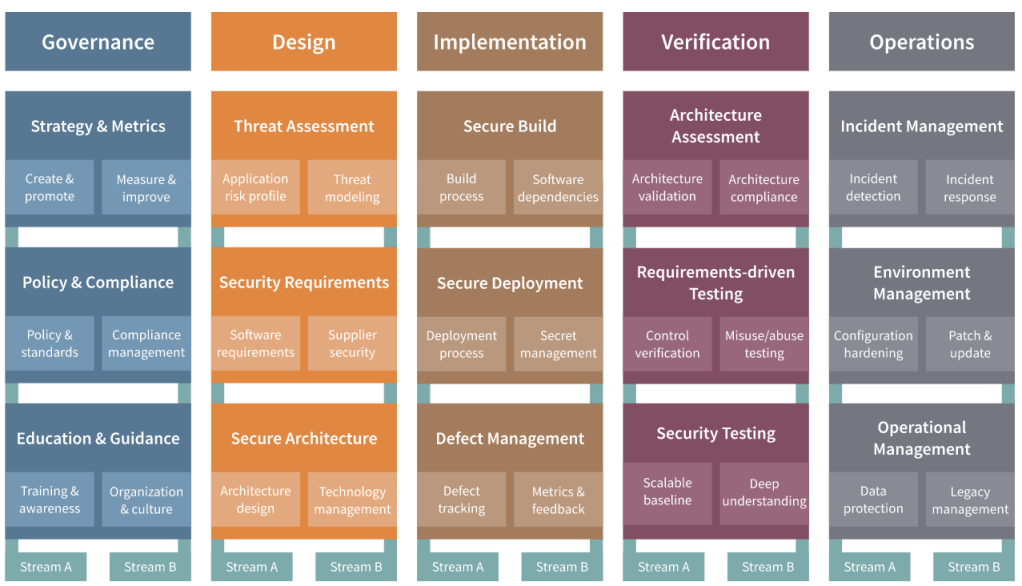
Using a single GitHub source, the SAMM team now automatically generates the Maturity Model that includes PDF documents, a website, along with the companion toolbox and applications. Model content has been converted to YAML files, improving automation while also allowing tools or other SAMM consumers to automatically use the model.
SAMM 2.0 Press Release
You can see that SAMM is not intend to be a replacement of either your existing SDLC practice, or your current maturity model, such as software capability maturity model (CMM). Instead, SAMM should be interwoven into your existing process. Be part of fabric of your team’s day to day activities.
As a proud individual and capabilities producer (developer and engineer), being chased by project managers on financials and timelines, by testers on defects, and by security professionals on findings and compliances, usually are less motivated parts of our day. Maturity model and process aim to bake those seemingly overhead into routines. Streamline them, standardize them, quantify them, and showcase their benefits the same way development team showcase the features. What you see here is an organic integration of security practices into software assurance lifecycle.
OWASP has a list of exciting projects (https://owasp.org/projects/). The most famous one was OWASP Top 10, see my early post on it. It website has a wealth of information security information and practices you will benefit from.
About the OWASP Foundation: https://owasp.org
About OWASP SAMM: https://owasp.org/www-project-samm